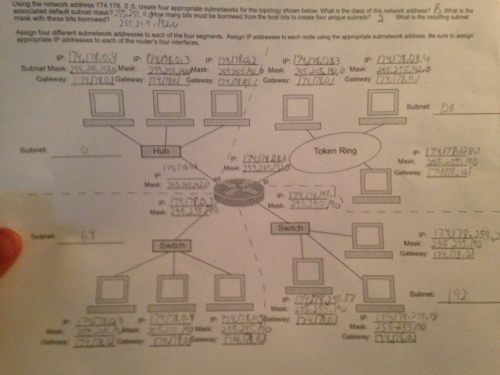
Objectives:
To create a stand-alone operational TCP/IP computer network with IPv4 addressing. The lab helped us better explore the TCP/IP network and how to config one.
Equipment List:
Switch, Router, Cabling
Notes and Observations:
My group and I created a working TCP/IP network by connecting three computers to switches which then when to a router. We then established eachothers IP addresses for our own computers and the IP for the router. We then used the hyperterminal to use the basic commands to connect everything together which I found the most difficult part of the lab due to some missing steps but received assistance by the instructor.
Questions and Answers:
Compare and contrast IANA and ARIN?
IANA, organization that distributes IP addresses worldwide. ARIN, organization that distributes IP addresses in the United States.
What are some reasons to update the TCP/IP protocol with a new IPv6 standard (to replace the older IPv4 standard)?
There are limited IPv4 addresses. IPv6 addresses have more characters so therefore can support the growing number.
What are some of the reasons to continue to use the IPv4 standard?
Most devices are already IPv4 setup and its easy to setup, but IPv6 is taking over.
What is the highest OSI layers that computers are communicating with when all of the computers have been connected together (using a hub or switch networking device), any TCP/IP addresses associated with the machines have been removed, the network interface cards of the computers are connected together (and the NICs have their link lights lit)?
Data Link Layer.
What protocol is used to automatically (or dynamically) assign IP addresses to computers?
DHCP
How do you check network connectivity? Can you think of other ways to confirm that the network works between the computers?
You can ping eachother by finding out the IP addresses to devices. You can also attempt to send messages to everyone and see who receives them.
Conclusions:
This lab was fairly easy. I’ve done this before. Only issue was with using hyperterminal. Great lab overall went well.